SACON was started as a community initiative to spread security architecture thinking. SACON focuses on several aspects of Security Architecture and Design including Secure Application Design, SecDevOps, Threat Modeling, Incident Response, IoT Security & More.
© Copyright CISO Platform
SACON sells out very fast, register and book your passes before it's sold out. If you register but do not purchase, that will allow you to get insider content from SACON and you can catch up when we are hosting one near you!
SACON - The Security Architecture Conference
WHO COVERED US
PREREGISTER- SACON 2018 !
Overview of AI & Machine Learning for CISOs and how they're impacting the security landscape
Summary of Top Talks from prominent security conferences like RSAC, BlackHat, Defcon etc.
Overview of Deception Technology, Architecture & Key Components, Deployment Guidelines
Designing Multiple layers of Security Architecture, from Business Architecture to Technical Security Architecture
AI & Machine Learning for CISOs
Top talks from global conferences
Deception
Cybersecurity Reference Architecture Design
Understanding Business / Management
& Communicating with the Board
Understanding key management concepts so that you can align your security program with business priorities & Creating a reference board presentation template which you can use for 2018
Managing insider threats using behavioural analytics
Insider Threats
Security Threats Landscape for 2017
Evolution of Security Threats landscape & top 10 threats that were new in 2017
Top 10 Security Predictions for 2018
Based on our research, we'll be presenting top 10 predictions for 2018 for you to consider when making your plans
SOC
Reference architecture and overview of key components of a SOC, e.g.: SIEM, Honeypots, Data Sources, Integrations, Threat Intelligence, EDR, Forensics Tools etc.
IR - Incident Response
Building a framework & processes for managing cybersecurity incidents
Security Architecture Workshop
Designing Multiple layers of Security Architecture, from Business Architecture to Technical Security Architecture
Cyber Range Drills
Wargame on responding to various types of security incidents at a strategic and operational level
Threat Hunting
Here we'll discuss the Key Components, Tool Set, Learning "Hunter" Skills and a Case Study
Cloud Security
Overview of Amazon’s approach to cybersecurity
AppSec
Creating a scenario of an organization and then use controls from OpenSAMM and BSIMM to choose the right elements of the AppSec program
Security Tech Landscape
Overview of new & emerging security technologies in the market and how the security tech landscape is shaping up
Overview of the IoT technology architecture and modelling threats & controls against different components (e.g.: Gateway)
Forensics
Workshop on how to do a comprehensive forensics examination post an incident, at endpoint & network level
SecDevOps
Leveraging the opportunity provided by DevOps to embed & automate security in the CI/CD processes
Startup Security
Startup Security Stack: Using 80-20 rule to build effective security strategy for a startup
Who Should Attend: CISO, CRO, Information Security Experts, IT Risk Professionals, Appsec Professionals ....
AGENDA AT A GLANCE
IOT
1,000+ Organisations Attended SACON
Moshe Ferber
Renowned Cloud Security Expert
Dr. Philip Polstra
Author Of 'Linux Forensic' & 'Windows Forensic'
Gregory Pickett
Renowned SecOps Expert
Murray Goldschmidt
Renowned DevSecOps Expert
Kenneth Bradberry
Chief Technology Officer, Xerox
Matt Suiche
Speaker & Review Board Member, Black Hat
Reinhold Wochner
Lead Of Digital Security, Raiffeisen Bank International
Bikash Barai
Co-Founder, Cigital-India (Earlier iViZ)
Keynote Speakers
Bringing together the best minds in the Security Industry
-Vijaykumar Reddy, Engineer, L&T Infotech
(Free PPTs) Top Talks @ SACON - 2017 !
SACON 2017 - Sold Out !
SACON (Security Architecture Conference) is the security architecture conference. It hosts great security minds from the world. Get access to selected talks from the conference.
AGENDA AT A GLANCE
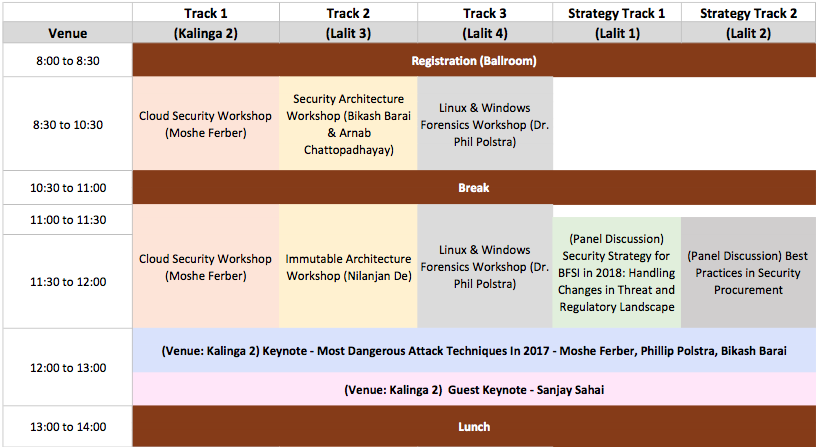
SACON - Day 1
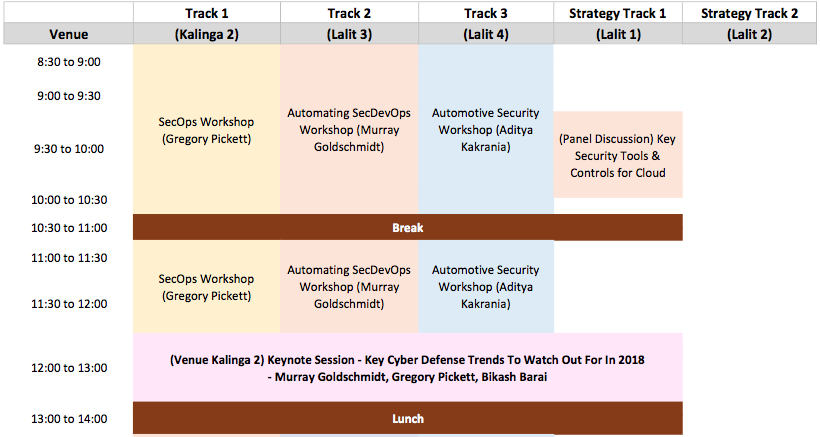
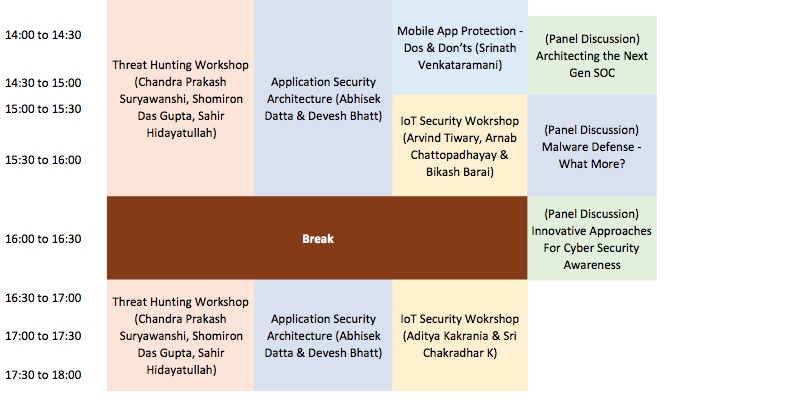
SACON - Day 2
SACON Workshop Pre-Requisites Click Here